清华大学人工智能研究中心
旗下发布了四大平台
(1)基于语言和常识知识库《知网》所研制的 OpenHowNet;
网址:https://hownet.thunlp.org/
OpenHowNet 源自在中文世界有巨大影响力的语言知识库——知网(HowNet)。
(2)中英文跨语言百科知识图谱 XLORE;
网址:https://xlore.org/
XLORE 是融合中、英、法维基百科和百度百科,对百科知识进行结构化和跨语言链接构建的多语言知识图谱, 是中英文知识规模较平衡的大规模多语言知识图谱。
(3)科技知识挖掘平台 AMiner;
网址:https://aminer.cn/
AMiner 旨在为研究人员社交网络提供全面的搜索和数据挖掘服务。
(4)THUAITR
THUAITR 是以 AMiner 全球科技情报大数据完觉服务平台为基础,采用人工智能自动生成技术,汇集而成的科技领域洞察报告。
《清华大学人工智能技术系列报告》(THUAITR):https://reports.aminer.cn/
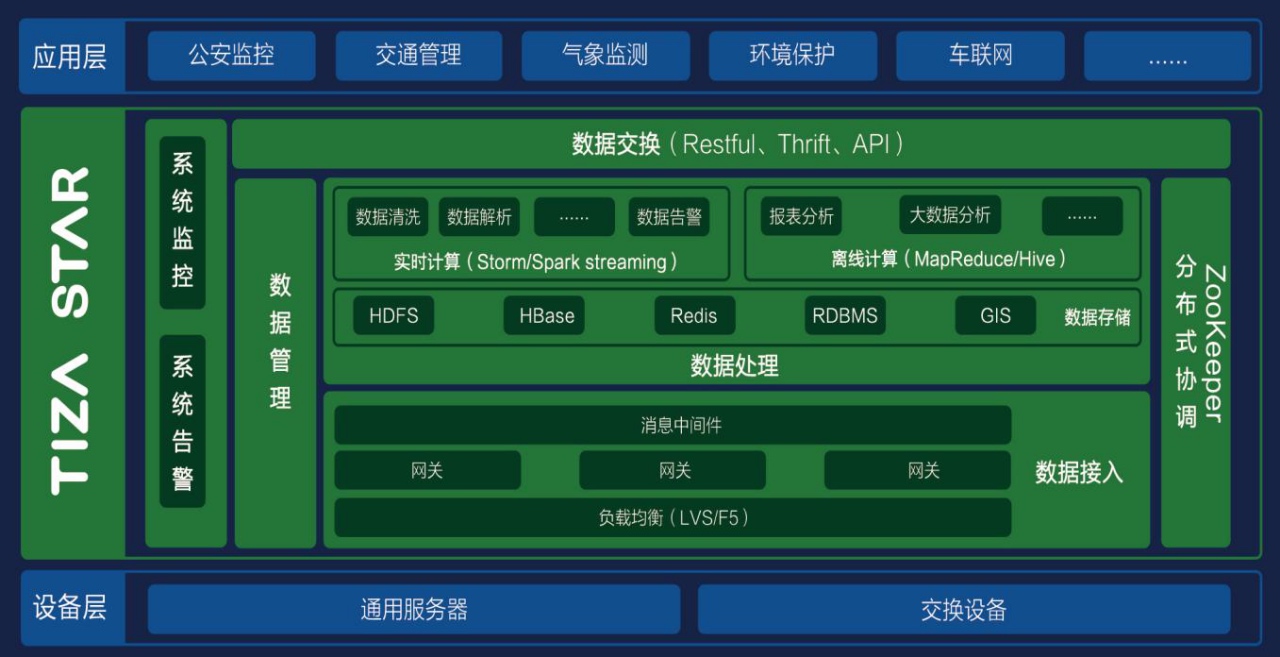
大数据平台
大数据平台架构
Hbase系
青云架构
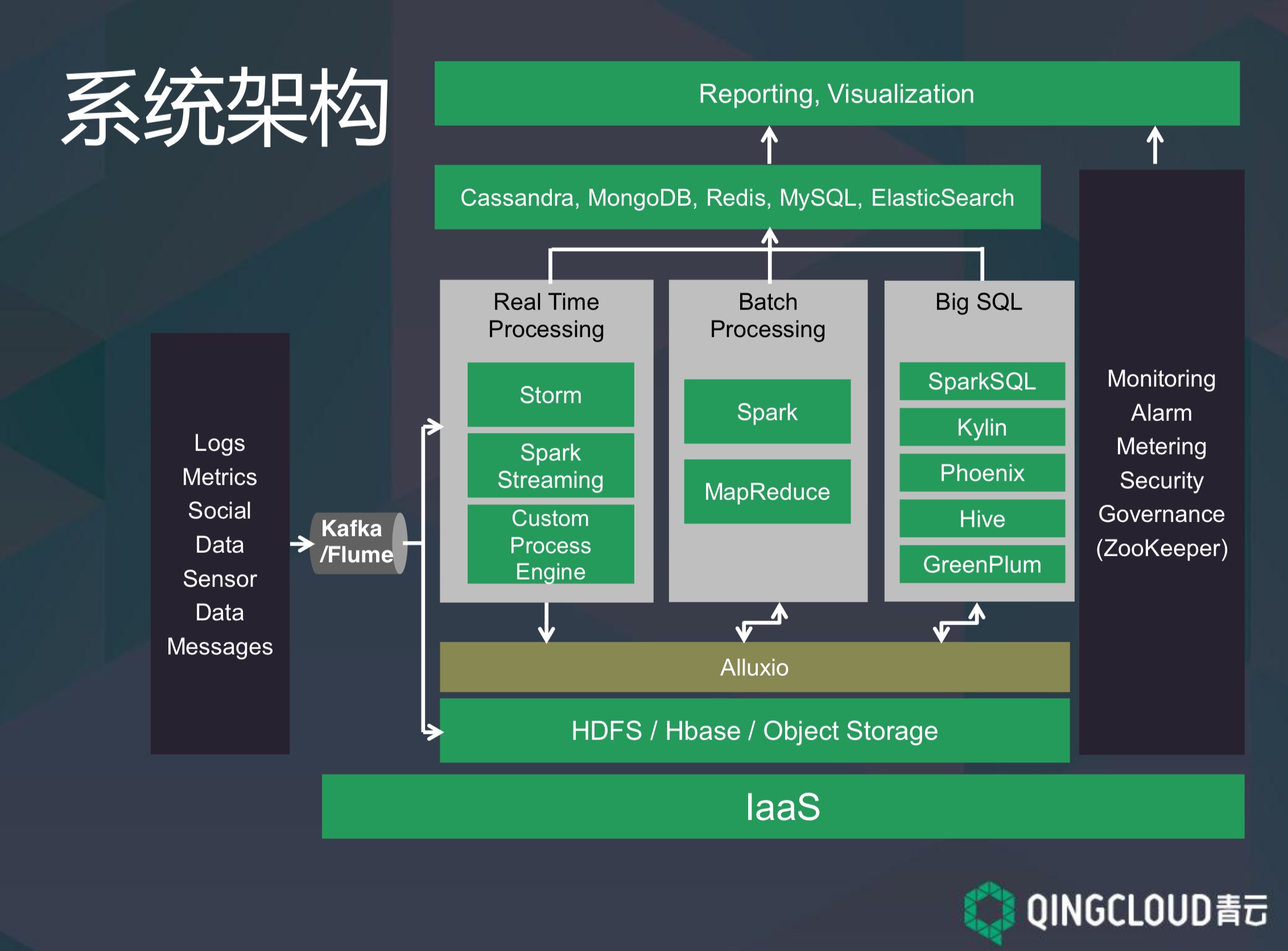
MongoDB系
采用自动分片技术
400億個傳感器。19萬億美元的收入。你將需要一個更大的數據庫。
400億個傳感器。19萬億美元的收入。你將需要一個更大的數據庫。
postgreSQL系
postgreSQL的解决方案出来了,但是感觉支持的比较少
对比分析
(分析比较到位)NoSql 分析 hbase,mongodb,redis
数据分析
选择可以看看这篇文章 https://www.kancloud.cn/nieguofu973873838/thinkphp_html_js/519541
Apache Storm
Apache Spark
Apache Samza
企业大数据管理
Hadoop 架构
决策写回记清楚,如何处理决策写回
Ambari好用的Hadoop安装部署工具
未来已来,变革中的数据可视化
今天,大数据已无所不在,并且正被越来越广泛的被应用到历史,政治,科学,经济,商业甚至渗透到我们生活的方方面面中,获取的渠道也越来越便利。通过本系列的前面几篇文章,我们已经了解了数据可视化的必要性,而目前市面上也已经具备了非常多成熟的BI绘制工具,如画面,QlikView的的和魔镜等等。虽然这些工具正在变得越来越自动化,然而,随着大数据时代的来临,信息每天都在以爆炸式的速度增长,其复杂性也越来越高;其次,随着越来越多科学可视化的需求产生,地图,3D物理结构等技术将会被更加广泛的使用。所以,当人类的认知能力越发受到传统可视化形式的限制时,隐藏在大数据背后的价值就难以发挥出来, 如果因为展示形式的限制导致数据的可读性和及时性降低,从而影响用户的理解和决策的快速实施,那么,数据可视化将失 其价值。
然而,所幸的是,技术的快速发展和不断变化的认知框架正在为人类打开新的视野,促使艺术与技术相结合而产生新型的数据可视化形式。
数据可视化的演变历史
一。为什么数据可视化形式亟待改进
我们每天都在说大数据,那数据到底能“大”到怎样的程度也许你已经听说过以下结论:世界上90%的数据是在过去几年内产生的事实上,过去三十年中,全世界的数据量大约每两年增加10倍,有专家估计,到2020年的时候,数据的年度产出量会达到4300%甚至更多,这已远远超出了著名的摩尔定律理论;所以,面临着这样的巨大挑战,大数据的时代的数据可视化给我们提出了以下要求:
1.以更细化的形式表达数据
首先,让我们来看一个相对简单的静态可视化图表:
图1.不安全流产率百分比估计( SciDev.Net 2016)
再来是一个更复杂的可视化图表:

图2.1986到2013年间172个国家的移动电话、固话和互联网的订购数量与容量( SciDev.Net 2015)
图1是一个数据量较少的静态可视化图表,我们可以通过4根柱状图的对比快速得到信息,而显而易见的,图2的数据量大大超出了图1,不仅有一百多个国家的数据变化,还包含不同的年份对比。更庞杂的数据量要求设计者通过更加细化的方式来呈现数据,所以我们可以看到图2以折线图为基础,结合了气泡的动态变化、语音说明,还包括让读者通过交互操作来选择展示哪些数据,才得以恰当和全面地展示这份数据,从而更完整的讲述一个故事。
2.以更全面的维度理解数据
“随着大数据技术成为我们生活的一部分,我们应该开始从一个比以前更大更去全面的角度来理解事物。” 这句话来自《大数据时代》,作者的原意是在大数据时代我们应该舍弃对数据精确性的要求,而去接受更全面但是也更混杂的数据,笔者认为它同样可以用来形容未来在数据可视化方面可以进步的方向。
众所周知,人类的视觉认知能力是有限的,类似下图这样的高密度可视化图形,虽然看似丰富和具有“艺术感”,可中间重叠连接的数据往往导致图形变得复杂和难以理解。
每个节点代表一个Wiki页面,每一根线代表页面之间的连接( 维基百科链接结构可视化 )
但是如果像下面这两个宇宙科普项目这样:你可以通过放大或缩小星系、调整视角、甚至像飞进了这些星球之间一样去观察它们,点击它们查看详细介绍等等……这样一个更”立体”的数据展示是否能更好的帮助你去理解这些信息呢?
通过交互式3D可视化展示探索宇宙中超过十万颗星球( 100000 Stars )
通过手势识别设备来探索开普勒计划目前已确认的近2300个候选系外行星
如今,人们逐渐已不再满足于平面和静态的数据可视化视觉体验,而是越发想要“更深入”去理解一份数据,传统的数据可视化图表已不再是唯一的表现形式,现代媒介和技术的多样性,使人们感知数据的方式也更加多元。
3.以更美的方式呈现数据
艺术和数据可视化之间一直有着很深的联系,随着数据的指数级增长和技术的日趋成熟,一方面,用户们对可视化的美学标准提出越来越高的要求;另一方面,艺术家和设计师们也可以采用越来越创造性的方式来表现数据,使可视化更加具有冲击力。 纵观历史,随着人们接受并习惯了一种新的发明后,接下来就是对其进行一步步的优化和美化,以配合时代的要求, 数据可视化也是如此,因为它正在变得司空见惯,良好的阅读体验和视觉表现将成为其与竞品所区分的特征之一。
CNN ECOSPHERE项目将 “里约+20”地球峰会期间的Twitter话题汇集成星球上的一颗颗大树
二.大数据时代的数据可视化具有哪些特征
在这里,笔者大概将其整理归纳为以下三点,当然它们并非都是必备特征:

三.典型应用场景
那么,这些运用新技术的数据可视化目前主要是在哪些场景和形式下使用呢?
1.大屏
首先,不得不提到的一定的是大屏了。什么是大屏?顾名思义,就是指通过整个超大尺寸的LED屏幕来展示关键数据内容。随着许多企业的数据积累和数据可视化的普及,大屏数据可视化需求正在逐步扩大,例如一些监控中心、指挥调度中心这样需要依据实时数据快速做出决策的场所,以及如企业展厅、展览中心之类以数据展示为主的展示场所,还有如电商平台在大促活动时对外公布实时销售数据来作为广告公关手段等等,而具体的展示形式又可能分为带触摸等交互式操作或只是作单向的信息展示等等。

双十一购物狂欢节采用实时数据大屏,带给观众更加准确、震撼和清晰的体验
2.触摸屏
作为实现交互式数据可视化的方式之一,触屏设备常常用作控制大屏展示内容的操作设备(其中也包括手机和平板),也可以兼顾显示和操作一体来单独展示数据,大大增加了用户与数据之间的互动程度。
将触摸屏与3D可视化相结合的微软黑科技
3.网页
目前应用于数据可视化方面的网页技术可以说是琳琅满目,如D3.js、Processing.js、Three.js、ECharts(来自百度EFE数据可视化团队)等等,这些工具都能很好的实现各类图表样式,而Three.js作为WebGL的一个第三方库则相对更侧重于3D方向的展示。
1992-2010年内世界小型武器和弹药的进出口贸易数据展示( armsglobe.chromeexperiments.com )
4.视频
有数据显示,人们的平均注意力集中时间已从2008年的12秒下降到2015年的8秒,这并不奇怪,当我们在面对越来越多的信息来源时,会自然倾向于选择更快捷的方法来获取信息,而人类作为视觉动物天生就容易被移动的物体吸引,所以视频也是数据可视化的有效展示手段之一,并且视频受到展示平台的限制更少,可以应用的场景也更广。不过因为其不可交互的特性,视频展示更适合将数据与更真实、更艺术的视觉效果相结合,预先编排成一个个引人入胜的故事向用户娓娓道来。
地球交通路线发展史
四.数据可视化的未来
可惜,仅有以上这些展示方式是不够的,人眼仅仅透过平面的屏幕来接收信息仍然存在着限制,VR、AR、MR、全息投影…这些当下最火热的技术已经被应用到游戏、房地产、教育等各行各业,可以预见的是数据可视化也能与这些技术擦出有趣的火花,比如带来更真实的感官体验和更接近现实的交互方式,使用户可以完全“沉浸”到数据之中。可以想象一下,当我们可以以360ᵒ全方位的角度去观看、控制、触摸这些数据时,这种冲击力自然比面对一个个仅仅配着冷冰冰的数字的柱状图要强得多。而在不远的未来,触觉、嗅觉甚至味觉,都可能成为我们接受数据和信息的感知方式。
DeathTools将新闻事件中抽象的死亡人数数据变成一具具尸体摆放在VR空间中,给用户更直观的冲击
结语
感谢技术的飞速发展带给了我们更多元的选择,使我们可以运用前所未有的创造性方式来展示数据,但这并不意味着传统的数据可视化形式会逐渐消逝,毕竟这些新的展示技术和形式目前仍然面临着较高的制作成本,而传统的展示形式仍然是解决需要快速输出的可视化需求时的理想选择。数据可视化是一门同时结合了科学,设计和艺术的复杂学科,其核心意义始终在于清晰的叙述和艺术化的呈现,这些需要依靠数据分析师和设计师的精心策划而不是只有炫酷的效果,最终达到帮助用户理解数据和做出决策的目标,才能发挥它巨大的价值和无限的潜力。
参考资料:
“大数据时代” - Viktor Mayer-Schönberger
数据可视化:对循证决策的贡献 - SciDevNet
通过增强和虚拟现实可视化大数据:挑战和研究议程
所有错误的传统数据可视化和VR如何要解决这个问题
Tags: 数据可视化
Magic Quadrant for Contact Center Infrastructure, Worldwide
Published: 16 May 2017 ID: G00309857
Analyst(s):
Summary
Contact center infrastructure vendors are expanding their functional depth and breadth to deliver omnichannel solutions while enhancing their cloud delivery capabilities. Application leaders should evaluate vendors' technology and their ability to deliver in relevant regions.
Market Definition/Description
Gartner defines contact center infrastructure (CCI) as the products (equipment, software and services) needed to operate call centers for telephony support and contact centers for multichannel support. An additional major deployment option for CCI is as a core component of customer engagement centers (CECs), in which functionality is tightly integrated with CRM and social media channels to give a "single view of the customer" across all touchpoints. This type of infrastructure is used by customer and employee service and support centers, inbound and outbound telemarketing services, help desk services, government-operated support centers, and other types of structured communications operations.
Contact center interactions can be people-assisted or automated self-service, using web chat or interactive voice response (IVR) and speech recognition technologies, for example. They can also be a combination of people-assisted service and self-service. Channels for interaction use both live agents and messaging technology, and include voice, web, email, instant messaging, web chat, social media, video and mobile devices. Although there can be significant technology overlap between the CCI market and the CRM CEC market, the CCI market has three unique characteristics:
Solutions in the CCI market are often an extension of a unified communications (UC) technology portfolio. Although these solutions can route multichannel interactions, voice and telephony tend to play an important role.
Although CCI solutions include tools for integrating with CRM and other enterprise software packages, they do not typically include this functionality in their own solution stack.
Voice and data network performance and cost issues are key elements in the design of architecture and solutions.
In contrast, CEC solutions are frequently an extension of the CRM market; while they also route multichannel interactions, they focus on channels other than voice, and they support a strong focus on using existing customer data to optimize interactions based on the customer's desired outcome. These differences are significant in that they tend to result in separate decision processes driven by different decision makers within organizations. There is currently little overlap between the vendors appearing in the present Magic Quadrant and those in "Magic Quadrant for the CRM Customer Engagement Center."
Over time, we expect the two solution sets to merge, but that merger is still several years off.
Contact centers require a wide range of functions, architectures, features and services to be effective. Three major architectural approaches that are common are: integrated best-of-breed components, all-in-one bundled suites, and cloud-based solutions.
CCI includes a wide range of related technologies, some of which are central to vendors' offerings and some integrated through OEM or partnership relationships with best-of-breed providers. Technology areas can include:
Voice routing technologies:
Telephony infrastructure
IVR and voice portals for self-service applications, including speech-enabled self-service
Outbound dialing/proactive contact
Virtual routing applications for multisite and work-at-home scenarios
Digital channel routing technologies:
Multimedia contact routing and prioritization engines with real-time and historical reporting
Computer-telephony integration/web services interfaces — including tools for integration with CRM software
Presence tools
Email response management
Web chat
SMS
Collaborative browsing
Social media
Live and prerecorded video
Workflow routing and management
Mobile customer service applications
Knowledge-based self-service
Sentiment analysis
Workforce engagement management technologies:
Workforce management scheduling tools
Session recording and quality monitoring, including speech analytics
Data mart and analytics systems
Increasingly, contact center managers prefer to purchase much, or all, of their CCI as a bundle from a single source, in the pursuit of easier and enduring integration, cradle-to-grave integrated reporting and analytics, and easier system management. Therefore, leading CCI vendors offering complete portfolios of solutions — comprising their own products and those of partners and other strategic suppliers — are being favored.
The emerging contact center as a service (CCaaS) model — involving hosted, multitenant systems — is gaining attention as cloud approaches become increasingly accepted by enterprises. Although this Magic Quadrant focuses on premises-based (aka "on-premises") CCI offerings, a vendor's ability to offer viable CCaaS services to customers who may wish to eventually migrate to such services positively impacts its score on the Completeness of Vision axis. However, a vendor that exhibits a very strong shift in business strategy to make CCaaS its primary offering, and to de-emphasize its premises-based solution, may receive a lower score for Completeness of Vision than in the prior edition of this Magic Quadrant. There are currently no CCaaS-only providers that offer a substantial-enough global presence to warrant inclusion in this Magic Quadrant; however, all vendors covered this year now provide some form of a hosted or CCaaS offering, either directly or through channel partners.
Magic Quadrant
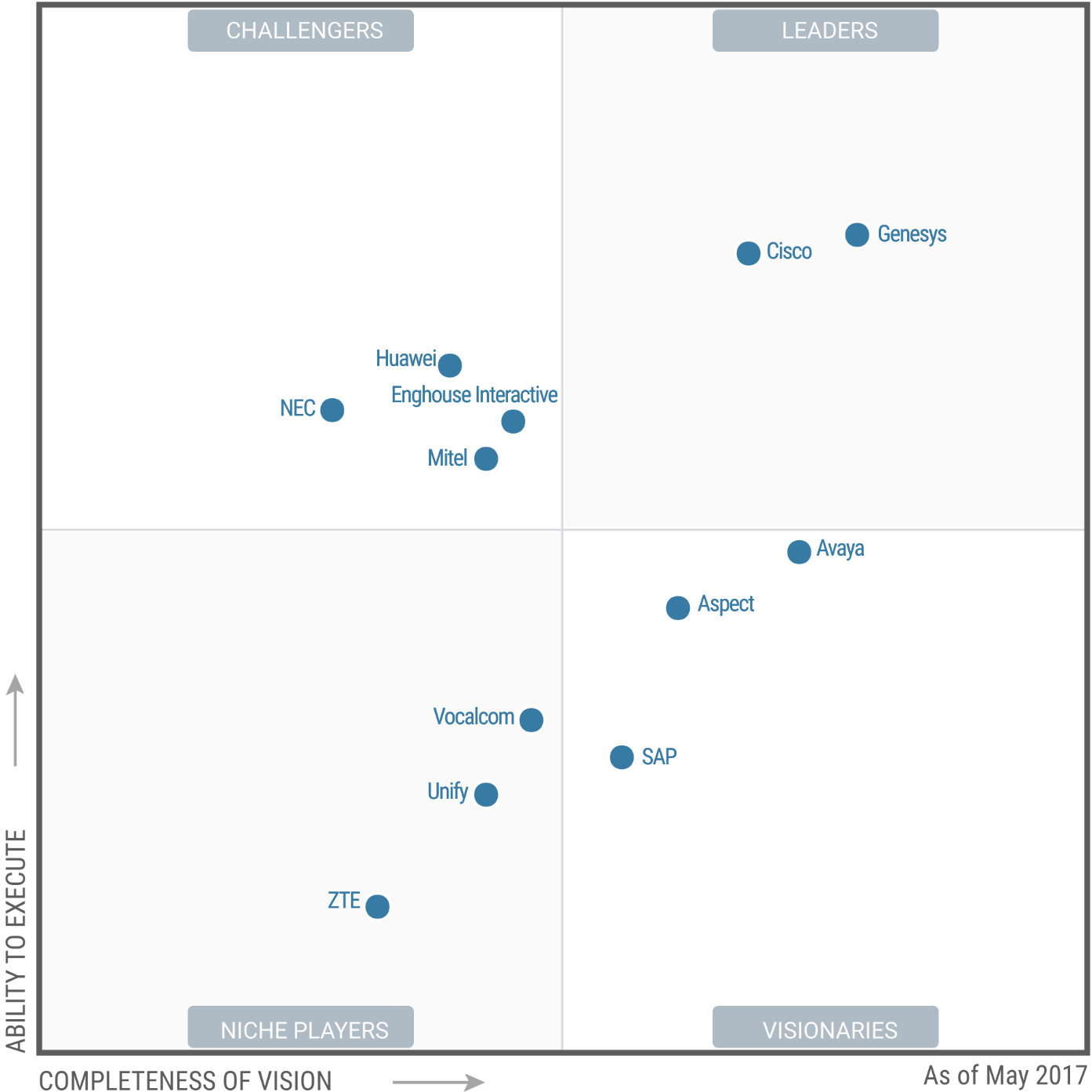
Figure 1. Magic Quadrant for Contact Center Infrastructure, Worldwide
Source: Gartner (May 2017)
Vendor Strengths and Cautions
Aspect
Aspect, a U.S.-based, privately held company, is owned predominantly by Golden Gate Capital and Oak Investment Partners. The company is in the process of recasting itself as a "cloud first" vendor, offering hosted and/or managed "private cloud" services as well as its Via and Zipwire CCaaS services, but it continues to generate a significant portion of its product revenue from its premises-based Unified IP platform. Unified IP offers a unified multimedia contact center application suite for midsize and large implementations, including several best-of-breed applications. Aspect filed for Chapter 11 structured bankruptcy protection in the U.S. courts in early 2016. It completed its financial restructuring and emerged from bankruptcy protection several months later; it has largely regained what sales momentum it lost during the bankruptcy period.
Organizations should consider Aspect when there is a need to integrate with multiple IP-PBX telephony environments, or when they want to "decouple" the timing of their contact center and telephony investment decisions.
Strengths
Aspect provides well-integrated, best-of-breed functionality in a variety of contributing contact center technology areas, including IVR, mobile customer service and web self-service, workforce engagement management (WEM) and outbound dialer.
Aspect's ability to integrate with a wide variety of third-party telephony and UC solutions enables it to support customers that want to consolidate their contact center technology while maintaining a decentralized approach to other communications technologies.
Aspect is good at delivering solutions to companies that require their systems to be customized in order to address business-specific needs, including companies that require global coverage for sales and support.
Cautions
It is unclear how well Aspect will be able to continue to aggressively fund the development and support of its premises-based contact center offerings and cloud offerings, because its installed base and derived service revenue (Aspect's largest source of income) are in decline.
Although Aspect has emerged from bankruptcy protection as a profitable business, some Gartner clients mistakenly assume that Aspect has been significantly weakened as a result of the bankruptcy process.
Some Gartner clients consider that Aspect is lacking relevance in a market that is moving from call and contact centers to CECs. Aspect has, however, made progress in evolving its products and services in recent years.
Avaya
Avaya is a privately held company with its headquarters in Santa Clara, California, U.S. It is owned by the private equity firms TPG and Silver Lake. In January 2017, Avaya filed for Chapter 11 bankruptcy reorganization in the U.S. courts in an effort to reorganize its balance sheet and restructure debt. As a result of this process, it is likely that the company's ownership structure will also change; the public notice of the ongoing bankruptcy proceedings are available online. 1
Avaya's core offering is its recently launched Oceana platform, adding advanced multichannel functionality to its Call Center Elite voice platform, and eventually to Avaya Aura Contact Center (AACC) and third-party automatic call distribution (ACD) solutions. The Oceana platform includes Oceanalytics for advanced multichannel reporting and customer journey mapping, and the Oceana Workspaces browser-based multichannel agent desktop interface.
Avaya continues to offer and support its existing multiple contact center platforms, each aimed at a different part of the market: Avaya Aura Call Center Elite for large enterprises with a voice-centric customer engagement strategy; AACC — and the Avaya Contact Center Select variant for Avaya IP Office — for midsize multichannel enterprises; Avaya IP Office Contact Center for small or midsize businesses (SMBs). Evolution paths to Oceana are available for existing Avaya customers.
Organizations of all sizes with sophisticated call-handling or multichannel requirements should consider Avaya's contact center offerings, which include several best-of-breed applications for contact center environments. Risk-averse organizations may not want to consider evaluating Avaya's solutions until it shows significant progress in reorganizing its capital structure and exiting Chapter 11 bankruptcy. 2
Strengths
Avaya has strong brand recognition with large and midsize corporate organizations for CCI. Its strong global footprint, including service provider_system integration (SP_SI partners), helps it satisfy the needs of most types of organization.
Avaya's Oceana multichannel contact center platform offers full digital channel support, context, attribute-based routing, and real-time and historical reporting and analytics. This platform consolidates Avaya's previously fragmented approach to delivering multichannel contact center functionality.
The Avaya Breeze platform (with Avaya Engagement Designer), Zang cloud communications platform and applications-as-service, and Avaya Snap-ins and Snapp Store marketplace, enable developers to quickly create unique communications-enabled contact center applications and workflows for within and beyond the enterprise.
Cautions
At the time of writing, Avaya is under Chapter 11 bankruptcy protection as it seeks to restructure its debt. If this process becomes protracted (a year or more), Avaya may be at risk of underfunding its new contact center development initiatives.
Although Avaya has created a coherent strategy for supporting CCaaS, the offering is still in its early stages.
An increasing number of Gartner clients are expressing dissatisfaction with Avaya's ability to deliver contact center solutions.
Cisco
Cisco is a U.S.-based public company with shares traded on the Nasdaq stock exchange.
Cisco's contact center offerings include: Unified Contact Center Enterprise (UCCE) for large enterprises and those requiring advanced functionality; Packaged Contact Center Enterprise (PCCE) for contact centers with up to 2,000 agents; Unified Contact Center Express for small and midsize contact centers with fewer than 400 agents; Unified Intelligent Contact Management Enterprise, which provides network-level routing and can support multivendor environments; Spark Care, a customer care capability for helpdesks and small teams that supports blended chat and call handling using the cloud-based Spark platform. A cloud-based variant of PCCE is also available through select channel partners on Cisco's Hosted Collaboration Solution platform.
Organizations that favor an end-to-end network, telephony, UC and contact center solution from a single vendor should consider Cisco's contact center offerings, especially those with advanced and scalable contact center requirements.
Strengths
Cisco has strong finances, corporate brand recognition and a robust global network of channel partners. As a result, it is frequently shortlisted by organizations looking to replace legacy contact center investments.
Cisco's alliance with Salesforce is a positive step toward offering integration between CRM and CCI. The brand strength and size of both companies is likely to result in mutually beneficial outcomes for them and their customers.
Cisco's new practice of bundling email and chat with its contact center licenses — together with gadgets for its Finesse desktop development environment — enable organizations to consider Cisco for managing contacts within an omnichannel experience.
Cautions
Cisco relies largely on partners to deliver core and contributing contact center functionalities such as workforce engagement and knowledge management — at a time when the industry is witnessing consolidation in these areas. Acquisition of one or more of these partners by competitors could result in disruption to existing partnerships and portfolio management.
Organizations committed to using Microsoft's Skype for Business as a UC infrastructure do not have a practical path for integration with a Cisco-based contact center platform.
Although Cisco's Spark Care cloud-based customer service platform is a promising development, it is likely to be a number of years before organizations can consider it a scalable next-generation solution for omnichannel CCaaS.
Enghouse Interactive
Enghouse Interactive is a division of Enghouse Systems, a public company based in Canada, with shares traded on the Toronto Stock Exchange. Enghouse has three primary contact center offerings: Contact Center: Enterprise (CCE) targets high-end enterprise premises-based contact center environments and virtualized cloud environments; Communications Center (CC) targets small or midsize contact centers, either on-premises or delivered through a hosted managed service, especially for integration with a number of PBXs (including with Skype for Business), and is sold exclusively through channel partners; Contact Center: Service Provider (CCSP) is a cloud-based multitenant platform aimed at service providers that offer CCaaS solutions.
Enghouse owns three other discrete technology providers: Trio Enterprises, Voxtron and the more recently acquired Presence Technology.
Consider Enghouse CC when looking for a multichannel contact center solution for fewer than 500 agents and where you need to tightly integrate with a Skype for Business UC infrastructure. Consider Enghouse CCE when looking for a complex, multisite or virtualized multimedia contact center routing solution.
Strengths
Enghouse Interactive's parent company, Enghouse Systems, is committed to a strategy for growth through acquisition, which supports growth and continued investment in Enghouse Interactive.
Enghouse has clarified its go-to-market plan for its core contact center offerings, which should make it easier for organizations to identify the most appropriate solution.
Enghouse's channel partners have amassed a large installed base for integrations of CC with Microsoft's Skype for Business infrastructure. A number of these have migrated with CC from legacy PBX platforms to Skype for Business. This can be useful for organizations looking for reference examples for a planned integration.
Cautions
Enghouse lacks brand recognition among contact center decision makers. This limits its ability to use its acquisitions to strengthen growth under a common brand.
The architectures of both Enghouse CC and Enghouse CCE rely heavily on integration with competitors' IP-PBX platforms for delivery of voice to the desktop. Although this enables contact center migration across PBXs, it can be challenging to market and sell as an independent contact center solution.
Enghouse pursues an acquisition strategy to promote organizational growth. Although the acquisition of smaller, discrete players can strengthen their financial stability, and provide value-added components for the portfolio, those smaller players may still struggle to compete in a market dominated by larger vendors.
Genesys
Genesys is a privately held company based in the U.S. and with major private equity investment from Permira and Hellman & Friedman. Genesys acquired Interactive Intelligence, a contact center and UC vendor, in December 2016, merging largely complementary product lines and providing Genesys with a more mature CCaaS offering.
Genesys has three primary offerings: PureEngage, offered on-premises or as a hosted/managed service, is based on Genesys' traditional offerings and supports contact centers with hundreds or thousands of agents, and particularly those with complex customization requirements; PureConnect, offered on-premises or as multi-instance CCaaS, is based on the traditional Interactive Intelligence Customer Interaction Center, supporting contact centers operating up to several hundred agents, particularly for customers with moderately complex needs who value a tightly integrated all-in-one platform; PureCloud, based on the Interactive Intelligence microservices-based, multitenant CCaaS offering, typically operating with contact centers of up to 250 agents for customers who value cloud-based, easy-to-deploy functionality and require only basic customization.
Consider Genesys for contact center solutions that span a variety of levels of complexity and scalability, including those that require significant customization to address differentiated customer service needs.
Strengths
Genesys has a well-defined approach for decoupling contact center applications from telephony infrastructure across a wide range of contact center sizes, levels of complexity and degrees of customization.
Genesys PureEngage includes an advanced set of "omnichannel journey management" tools. Gartner clients often look to Genesys for leading-edge solutions in this emerging sector.
Genesys PureConnect and PureCloud provide a common set of application development, management and reporting tools across a range of applications. These all-in-one offerings resonate strongly with decision makers in SMBs.
Cautions
The merging of the business operations of Genesys and Interactive Intelligence is still in the early phases of implementation. Customers for Genesys' solution sets must be prepared to monitor the performance of the vendor and its channel partners to ensure that performance does not suffer during this transitional phase.
Some Gartner clients report frustrations about the skills levels of Genesys resources providing support for its PureConnect and PureCloud offerings.
In the past, Genesys has not been seen as a strong provider of midmarket on-premises and CCaaS solutions. Gartner has found that this causes some customers in this market segment to overlook Genesys' solutions.
Huawei
Huawei is a privately held company based in China, with shares held primarily by the company's employees. Huawei's eSpace contact centers run on the following platforms: Soft ACD UAP9600 and UAP6600 platforms for large enterprise and communications service provider (CSP) environments; eSpace U2980 platform with software-based media gateway controller and media resource platform for enterprises; eSpace U2980 platform packaged as an all-in-one contact center appliance offering for small and midsize contact centers; Contact Center Express (CCE) solution for contact centers with fewer than 50 agents; Cloud Enterprise Communications Platform 6.0 (EC6.0) for private clouds, public clouds, and hybrid clouds supporting convergence and collaboration between multiple services.
Huawei also provides specialized APIs to enable partners to integrate with industry-specific applications, including those supporting the high-end finance and "safe city" vertical markets.
Price-sensitive CSPs, enterprises and government agencies, particularly those in Asia/Pacific (especially China) and emerging economies, should consider Huawei when looking for cost-effective solutions.
Strengths
Huawei offers a broad range of enterprise communications solutions, including contact centers, data networking and unified communications. This can be attractive to companies wishing to consolidate their communications investments with a single vendor.
Huawei has a strong contact center presence in China, and is continuing to grow its presence in other markets in Asia/Pacific, as well as in Latin America and Eastern Europe.
In 2016, Huawei ported its eSpace enterprise contact center offerings to its converged EC6.0 platform. This provides a more cost-effective and consolidated platform for contact center, UC and video collaboration, whether on-premises or in the cloud.
Cautions
Although Huawei is expanding globally, it considers the North American market to be a low priority, due to the geopolitical setback in the U.S. It has also had limited success in growing its presence with end-user organizations in Western Europe. This makes it difficult for Huawei to support the needs of many global enterprises.
Huawei lacks strong brand recognition for its enterprise contact center offerings outside its core market of China.
Huawei supports basic routing functionality for digital channels such as email, web chat and SMS, but requires partners to add advanced functionality (such as automatic responses, suggested responses and supervisor review) before sending. This adds to the complexity of deploying and supporting these functions.
Mitel
Mitel is a public company based in Canada, with shares traded on the Nasdaq and Toronto stock markets. Mitel's portfolio of premises-based solutions includes: MiContact Center Office for small, informal contact centers; MiContact Center Business, a prepackaged application set for the midmarket; MiContact Center Enterprise, which supports a broad suite of applications for enterprises with up to 30,000 concurrent agents.
Mitel also supports three CCaaS offerings, including an OEM CCaaS offering aimed at large or multichannel environments.
Consider Mitel's solutions when looking for a wide range of common contact center capabilities, particularly when integrating with a Mitel UC offering or when evaluating integration with Microsoft Skype for Business.
Strengths
Mitel's recent investments in improving its go-to-market capabilities in North America and Western Europe have improved its ability to win larger contact center deals than it has competed for in the past.
Organizations committed to Skype for Business for UC are able to consider Mitel's MiContact Center Business Edition as a contact center solution. Those committed to Cisco's UC infrastructure can consider MiContact Center Enterprise Edition.
Mitel has shown success in selling to the healthcare, local-government, community banking and retail sectors.
Cautions
Only organizations that already use Mitel for telephony and UC are likely to be offered its contact center solutions.
Although Mitel can be regarded as a global player, it has not aggressively targeted new market opportunities for its acquired products. Organizations outside Mitel's core markets may struggle to find relevant customer references and local channel partner skills to support Mitel's solutions.
While Mitel's API approach to the extensibility of its MiContact Center solutions is a promising development, it will need to continue to address the market with separate contact center offers until the transition to a microservice API-based architecture is complete.
NEC
NEC is a public company based in Japan, with shares traded on the Tokyo Stock Exchange. NEC's flagship multimedia contact center offering is Univerge Contact Center, which supports customers ranging from SMBs to companies with thousands of call center agents.
Enterprises with an existing NEC telephony system, those using big data in their contact centers, and those seeking an all-in-one solution for UC and collaboration and contact centers should consider NEC.
Strengths
NEC can provide differentiating industry-specific solutions in vertical markets such as hospitality, healthcare, education and government.
NEC has a large global installed base of telephony and UC customers to which it can sell its contact center platform.
Univerge Contact Center can draw on NEC's strength in data and speech analytics for functionality such as agent scripting, automated responses for digital interactions and advanced quality management.
Cautions
NEC has low brand recognition in the North American and Western European contact center markets. This limits its ability to sell to global companies with significant presence in these key markets.
NEC sells its contact center offerings primarily to organizations that already have significant NEC telephony environments. Gartner sees limited results from NEC's attempts to broaden the appeal of its contact center solutions and displace other vendors.
NEC relies largely on partners to deliver important contact center functionalities — such as workforce management, quality assurance and knowledge management — at a time when the industry is witnessing consolidation in these areas. Acquisitions by competitors could result in disruption to partnerships and portfolio management.
SAP
SAP, which is based in Germany, is a public company with shares traded on the Frankfurt and New York stock exchanges. SAP Contact Center is positioned within the SAP Hybris Customer Engagement and Commerce (CEC) business unit and delivers omnichannel customer engagement integrated with SAP's business application and SAP Cloud offerings.
SAP Contact Center is more suitable for organizations committed to the SAP suite of business applications and SAP Hybris Cloud for Customer offerings than it is for organizations looking for a stand-alone, multichannel contact center suite.
Strengths
SAP is a recognized global brand with a strong commitment to enterprise software. This includes the field of omnichannel customer engagement, of which contact center software is a core component.
Positioning its contact center platform as an element of SAP Hybris Service Engagement Center strengthens SAP's proposition for customer service within the broader portfolio of enterprise software.
SAP Contact Center is a scalable suite with multitenant properties provided by "Virtual Units." This aligns it well with SAP's portfolio of customer service applications based on the SAP Cloud Platform.
Cautions
Despite strengthening its marketing commitment to the contact center portfolio as part of the SAP Hybris CEC business unit, SAP has shown limited commitment to promoting its contact center solution as an alternative to solutions from larger vendors such as Avaya, Cisco and Genesys.
Tight integration with SAP Hybris Cloud for Customer and SAP Hybris Service Engagement Center for an omnichannel customer experience makes SAP Contact Center a less attractive proposition for organizations not committed to SAP customer service applications.
SAP relies largely on partners to deliver important contact center functionalities, such as workforce engagement, dialer and knowledge management (via a separate division of SAP), at a time when the industry is witnessing consolidation in these areas. Acquisitions by competitors could result in disruption to partnerships and portfolio management.
Unify
Unify is a wholly owned subsidiary of Atos, a global system integration and outsourcing business based in France. Unify's contact center offerings include: OpenScape Contact Center Enterprise, which is Unify's flagship multichannel platform for on-premises or private cloud deployment by midsize and large organizations with up to 7,500 users; OpenScape Media Portal, a key technology for IVR and voice service; OpenScape Enterprise Express, an all-in-one appliance that includes contact center support.
Unify has a partnership with inContact for the OpenScape Cloud Contact Center offering. It also partners with Genesys to offer PureEngage for very high-end, complex requirements.
Organizations committed to, or considering, the Unify portfolio should consider OpenScape Contact Center Enterprise as a contender for OpenScape infrastructures.
Strengths
As a subsidiary of Atos, Unify is in a financially strong position to execute a growth plan for its communications and contact center business.
The OpenScape Contact Center Agent Portal, launched in 2015, is a promising development in support of an omnichannel customer experience.
Transitioning from Unify services for contact centers to Atos is an opportunity for organizations to benefit from best practices from a global player in IT services.
Cautions
Unify's OpenScape Contact Center Enterprise is moving toward platform independence with preferred devices, but it still requires separate appliance servers for contact center, voice portal and outbound dialer functions.
Unify has overlapping contact center solutions in its portfolio. It is unclear at this time whether Atos favors continued development of the Unify product portfolio or use of solutions from partners Genesys and inContact.
Unify relies largely on partners to deliver important contact center functionalities such as workforce management and quality monitoring, and lacks a knowledge management offering at a time when the industry is witnessing consolidation in these areas. Acquisitions by competitors could result in disruption to existing partnerships and portfolio management.
Vocalcom
Vocalcom, which is based in France, is a privately owned company with Apax Partners as the majority shareholder. Vocalcom uses a common software platform to power its Vocalcom Cloud Contact Center, Vocalcom Cloud Contact Center for Salesforce, Vocalcom Virtual Contact Center and Vocalcom Virtual Contact Center for Avaya.
Vocalcom's contact center suite solutions are offered primarily as cloud-based solutions, but can also be deployed on-premises and with perpetual-license terms. Vocalcom Cloud Contact Center solutions can be deployed in Amazon's Elastic Compute Cloud (EC2) or Salesforce's Force.com cloud infrastructures.
Organizations looking for platform-independent multichannel solutions with integration to Salesforce should consider Vocalcom's suite of contact center software.
Strengths
Vocalcom's Cloud Contact Center approach has enabled it to expand into new markets by using flexible third-party infrastructure as a service (IaaS), specifically Amazon EC2 and Salesforce Force.com.
Vocalcom continues to be appreciated by customers, judging from GetApp's rankings for CRM, customer service and cloud contact center software.
Vocalcom's history of offering solutions to outsourcers on a utility license basis positions it well to offer organizations flexible, consumption-based licensing for its on-premises, private cloud and public cloud solutions.
Cautions
Vocalcom is challenged to achieve brand recognition among competitors with larger sales and marketing budgets.
Vocalcom relies on partners to deliver workforce management functionality at a time when the industry is witnessing consolidation in the area of workforce engagement. Acquisitions by competitors could result in disruption to existing partnerships and portfolio management.
Vocalcom is struggling to establish a presence in North America. This will limit its appeal to organizations with requirements in this region, including global organizations.
ZTE
ZTE, which is based in China, is a public company with shares traded on the Hong Kong Stock Exchange. Its Next Generation Call Center (NGCC) suite supports highly scalable multimedia contact center capabilities, with strong support for both inbound and outbound operations in cloud- and premises-based configurations. ZTE's offerings include: the AnyService@ZXNGCC multimedia unified contact center product, which is based on its ZXMSQ10 SoftACD switch and system, or its AnyService@ZXNGCC all-IP-based contact center switching solution; the ZXQ20 appliance-based all-in-one contact center solution for small or midsize contact centers.
Consider ZTE's NGCC suite for deployments in China and emerging economies, particularly when the requirement is for price-competitive solutions that scale to thousands of agents (for example, in CSP and contact center business process outsourcing environments).
Strengths
ZTE's NGCC suite is well-suited for CSPs needing to provide multitenant virtual contact center services for enterprise customers, especially those in the call center service outsourcing business.
ZTE's NGCC suite can be deployed as an all-software solution running on a next-generation-network softswitch or an IP Multimedia Subsystem (IMS) network for greater efficiency in CSP environments.
ZTE is good at selling solutions to CSPs in China and many emerging economies.
Cautions
ZTE lacks brand recognition for enterprise contact center sales outside China.
ZTE lacks a broad base of enterprise-focused channel partners or CSP partners with a strong understanding of the best practices used in contact center environments.
ZTE's ZXQ20 appliance-based bundled contact center offering for small or midsize contact centers has achieved limited adoption so far. Potential users should check their suppliers' experience with this product and check local customers' references.
Vendors Added and Dropped
We review and adjust our inclusion criteria for Magic Quadrants as markets change. As a result of these adjustments, the mix of vendors in any Magic Quadrant may change over time. A vendor's appearance in a Magic Quadrant one year and not the next does not necessarily indicate that we have changed our opinion of that vendor. It may be a reflection of a change in the market and, therefore, changed evaluation criteria, or of a change of focus by that vendor.
Added
None
Dropped
ALE — Did not meet the inclusion criteria for premises-based contact center product and service revenue
Altitude — Did not meet the inclusion criteria for premises-based contact center product and service revenue
Collab — Did not meet the inclusion criteria for premises-based contact center product and service revenue
Interactive Intelligence — Was acquired by Genesys
Presence Technology — Was acquired by Enghouse Interactive
ShoreTel — Did not meet the inclusion criteria for premises-based contact center product and service revenue
Inclusion and Exclusion Criteria
To be included in this Magic Quadrant, solution providers had to demonstrate all of the following capabilities:
Premises-based contact center product and service revenue of more than $45 million in the calendar year 2016.
Evidence of sales, marketing and operational presence in a minimum of three of the following geographical regions: Asia_Pacific, Eastern Europe, Japan, Latin America, the Middle East and Africa, North America, and Western Europe. We required evidence that vendors operated sales offices in those regions and were actively selling contact center solutions in those regions; they could not just sell solutions in one region for delivery in the other regions. We also required vendors to have a multiple-language web presence. Vendors could meet these requirements directly and_or through channel partners.
Significant market share in the geographic markets specified above.
Sufficient sales and operational presence to support market objectives.
Demonstrable solutions in a minimum of five of the CCI technology areas defined in the Market Definition/Description section of this document.
Ability to generate significant interest by leading client market segments.
Honorable Mentions
The following vendors are not included in this Magic Quadrant, because they ship products predominantly to a single country or did not meet other inclusion criteria, but they are appropriate for certain situations and they sometimes compete against vendors that are included in this Magic Quadrant:
Alcatel-Lucent Enterprise (ALE)
Clarity
Collab
ComputerTalk
Drishti-soft Solutions
Noble Systems
Noda
ShoreTel
Towards Vision Technologies (TVT)
Workstreampeople
Evaluation Criteria
Gartner analysts evaluate CCI technology providers based on the breadth, quality and overall maturity of their applications, customer support capabilities, and ability to deliver solutions that enable contact center operations in the formal contact centers of midsize or large enterprises. Ultimately, CCI technology providers are judged on their ability to capitalize on their vision and their success in doing so.
Table 1. Ability to Execute Evaluation Criteria
Evaluation Criteria
Weighting
Product or Service
High
Overall Viability
High
Sales Execution/Pricing
Medium
Market Responsiveness/Record
Medium
Marketing Execution
Medium
Customer Experience
Medium
Operations
Medium
Source: Gartner (May 2017)
Completeness of Vision
Gartner analysts evaluate CCI technology providers based on their ability to convincingly articulate logical statements about current and future market directions, innovations, customer needs and competitive forces, and how well these map to Gartner's overall understanding of the market. Ultimately, CCI technology providers are evaluated on their understanding of how market forces can be exploited to create opportunities for them and their clients.
Table 2. Completeness of Vision Evaluation Criteria
Evaluation Criteria
Weighting
Market Understanding
High
Marketing Strategy
Medium
Sales Strategy
Medium
Offering (Product) Strategy
High
Business Model
Medium
Vertical/Industry Strategy
Medium
Innovation
Medium
Geographic Strategy
Medium
Source: Gartner (May 2017)
Quadrant Descriptions
Leaders
Leaders are high-viability vendors with broad portfolios, significant market share, broad geographic coverage, a clear vision of how contact center needs will evolve, and a proven track record of delivering contact center solutions. They are well-positioned with their current product portfolio and likely to continue delivering leading products. Leaders do not necessarily offer a best-of-breed solution for every customer requirement. Overall, however, their products are strong and often have some exceptional capabilities. These vendors also provide solutions that pose a relatively low risk of deployment failure.
Challengers
Challengers are vendors with strong market capabilities and good solutions for specific markets. Overall, however, their products lack the breadth and depth of those in the Leaders quadrant. Challengers do not always communicate a clear vision of how the contact center market is evolving, and they are often less innovative or advanced than Leaders. Challengers often excel at selling contact center functionality to their existing PBX and IP telephony customers.
Visionaries
Visionaries demonstrate a clear understanding of the contact center market and provide key innovations that point to the market's future. However, they typically lack the ability to influence a large portion of the market, have not yet expanded their sales and support capabilities on a regional basis, or do not yet have the funding to execute with the same capabilities as the Leaders.
Niche Players
Niche Players offer contact center products that focus on a segment of the market or a subset of its functionality. Customers aligned with the focus of a Niche Player may find its offerings to be a good fit for their needs.
Context
The market for CCI is currently in an innovative and dynamic phase, in which multiple forces are affecting purchase and deployment decisions in new ways; these forces include:
Decoupling of CCI from telephony/UC — CCI purchases have traditionally been closely linked to a company's chosen telephony vendor. However, these purchase decisions have increasingly been decoupled in recent years. One factor driving the decoupling of CCI from telephony infrastructure is that, as companies increasingly tie their telephony decisions to their broader UC strategies, they often want their CCI purchases to offer them flexibility of deployment — should their UC strategy draw them away from their existing telephony vendor. A prime example of this is seen when companies plan to evolve their UC strategies to focus on Microsoft Skype for Business. Because Microsoft does not currently offer its own robust CCI solution, contact center decision makers and planners may opt to select a CCI solution from a company whose enterprise communications application business is not heavily tied to an enterprise telephony or UC product line.
Adoption of CCaaS — A second significant force for change in the CCI market is the increasing propensity of CCI decision makers to consider, and often select, CCaaS offerings as a replacement for premises-based solutions. In many cases, the CCI vendors that also have UC offerings lack mature CCaaS offerings, and Gartner clients often feel compelled to change vendors in order to access more mature CCaaS services. In some cases, this decision is driven by the aforementioned desire to decouple a company's CCI and telephony_UC decisions. In other cases, it is driven by other factors, including: the desire to switch from a capital expenditure acquisition model to an operating expenditure model, and the potential for a lower total cost of ownership; a desire to focus investments and staffing on core business products and services; the need to scale license usage up and down to match seasonal staffing demands; and_or the need for more rapid deployment.
Shift to a holistic view of customer engagement — The contact center market is evolving from a focus on discrete, one-off customer interactions using a variety of communications channel silos to a more integrated and holistic view of customer activities and workflows, given that a customer may engage in a variety of different activities in the course of completing a customer journey. This focus on context-aware, multichannel (including web self-service and social media), reactive and proactive interactions is shaping the evolution of contact centers into CECs. This change in focus is still in its early phases in terms of adoption and, at present, there is more vendor hype than actual customer service transformation. However, as phone-based customer service now shares popularity with other communications channels, many mainstream technology adopters are at least planning to orchestrate their various customer interaction channels more effectively by moving to a more convenient, cohesive and consistent customer experience.
Drive toward multichannel engagement — The drive to develop the contact center into a customer-experience-centric CEC is injecting additional dynamics into the contact center market. Companies are altering their evaluation and selection of vendors to provide nonvoice channels (email, web chat, video chat, social and so on) to their customer service environments. During the past five to 10 years, many enterprises have looked to either their CRM vendors or best-of-breed specialists to provide these customer interaction channels. However, voice-based interactions continue to make up a significant portion of interactions in contact centers. As such, as companies look to evolve their customer support to become more customer-centric across all interaction channels, some are recognizing the benefits of acquiring both their voice and nonvoice channels as a package from a single vendor — and very few CRM vendors support phone-based-assisted customer service. Benefits include the use of a consistent business rule management capability for routing, queuing and escalating interactions across channels, enabling a company to prioritize the handling of the best customers regardless of customers' chosen channels. Obtaining all interaction applications from a single vendor also makes it easier for companies to manage reporting and staffing across channels, rather than having to integrate operational performance data across separate systems.
Integration of workforce optimization and engagement capabilities — The integration of workforce optimization (WFO) and customer service WEM capabilities under the umbrella of contact center application suites is further along the evolution path toward a greater breadth of capabilities than is the integration of nonvoice channels. WFO solutions have traditionally been purchased as "point" solutions in the WFO application stack (for example, from separate WFM, recording, quality assurance, analytics and e-learning vendors) or from vendors offering integrated WFO suites. WEM solutions represent an evolution of WFO technologies, seeking to improve customer experience and loyalty by making agent resources more engaged in delivering differentiated experiences to the customers they interact with. In recent years, a number of leading CCI vendors have added functionality to their application suites that can now rival the offerings of WFO and WEM specialists, at least for companies needing midlevel functionality; and, in some cases, they now rival the WFO and WEM specialists in delivering high-end capabilities. It should be noted, however, that even those CCI vendors that have incorporated WFO and WEM capabilities into their application suites will also support tight integrations with the WFO and WEM specialists, because most of the installed base requires support for these integrations.
Addition of knowledge management and interaction orchestration capabilities — Many of the leading "traditional" contact center vendors are adding knowledge management capabilities (for enhanced multichannel self-service) and interaction orchestration capabilities (to make better use of customer context information from multiple enterprise data sources and support customer journeys across interaction channels) to their application suites. Although these enhanced suites are still in the early stages of adoption, they are beginning to pose a challenge to the more common decision to obtain the nonvoice channels from CRM vendors or best-of-breed specialists.
Market Overview
In 2017, Gartner substantially increased the minimum revenue criterion for inclusion in this Magic Quadrant from the previous \(10 million in sales and services revenue to a new minimum revenue criterion of \)45 million in CCI sales and services revenue. This increase better reflects the maturity of the market for CCI. The positioning of vendors on this year's version of the CCI Magic Quadrant has undergone several changes — some quite significant — driven in part by the removal of six vendors from the Magic Quadrant as a result of setting a higher bar for the inclusion requirements, as well as by changes in those vendors' strategy, performance and technology.
Vendors in the Leaders quadrant tend to have strong product functionality and roadmaps and appear frequently on our clients' shortlists. In the Leaders quadrant, both Cisco and Genesys held similar positions in terms of Ability to Execute compared with 2016, while slightly improving their positions on the Completeness of Vision axis as their developments in customer journey analytics begin to resonate with Gartner clients. Genesys' acquisition of Interactive Intelligence has strengthened the company's ability to reach both midmarket and CCaaS customers, yet it is still in the early stages of integrating the two previously competing businesses. As a result, Genesys' score for Completeness of Vision has improved, but we are taking a "wait and see" approach before strengthening its score for Ability to Execute.
Vendors in the Challengers quadrant tend to have good, although not leading, product functionality and roadmaps. They tend not to appear on Gartner client shortlists as frequently as do the Leaders, which indicates that their market visions do not resonate as strongly with our clients. In the Challengers quadrant, Huawei's position was reduced in both Completeness of Vision and Ability to Execute based on its limited presence in the markets of North America and Western Europe, and its stronger focus on service providers rather than enterprises (this document being focused on offerings for enterprises). Enghouse Interactive's score for Ability to Execute improved based on its continued growth and strong performance in providing small to midmarket contact center solutions in Microsoft Skype for Business UC deployments. Mitel's score for Ability to Execute declined relative to the prior version of this document, having been rated a Caution by Gartner's financial scoring methodology. NEC held its position by enhancing its offerings and Ability to Execute at a pace equivalent to the improvements seen in the market overall.
Vendors in the Visionaries quadrant are positioned on the basis of their differentiated functionality. Avaya's introduction of its Oceana multichannel contact center solution combined with its Breeze architecture for custom integrations, expands on an already strong set of offerings, improving the company's score on the Completeness of Vision axis. However, Avaya's bankruptcy reorganization and weakened customer experience rating has reduced its comparable position on the Ability to Execute axis. Aspect is a Visionary largely due to its strong capabilities in ancillary contact center applications, including IVR, WFO and dialer. Aspect continues to show that it is regaining sales momentum (during the past several years) and, as such, we have increased its score for Ability to Execute. SAP is a Visionary due to tight integration with the company's CRM and ERP offerings, including the Hana big data analytics platform. SAP's position has improved along the Completeness of Vision axis as a result of its contact center business being integrated into the larger SAP Hybris CEC business unit, although it remains to be seen if this organizational change will result in an improvement in its Ability to Execute.
Vendors in the Niche Players quadrant often have good, although not leading, product functionality, combined with limited ability to execute beyond a specific market niche. Vocalcom, Unify and ZTE all remained in the Niche Players quadrant this year, although their positions showed some changes. Vocalcom improved its rating for Completeness of Vision based on its expanding breadth of both on-premises and CCaaS functionality. Unify's position declined in Ability to Execute as a result of its declining sales; however, its score for Completeness of Vision remains consistent year over year. ZTE's score for Ability to Execute slipped slightly due to its focus on selling into the service provider market rather than to enterprises, as well as due to general repositioning of vendor placement resulting from the removal of several vendors from last year's Niche Players quadrant.
Acronym Key and Glossary Terms
CCaaS contact center as a service CCI contact center infrastructure CEC customer engagement center CSP communications service provider IVR interactive voice response SMB small or midsize business UC unified communications WEM workforce engagement management WFO workforce optimization
1 See Avaya Inc. (17-10089) , Prime Clerk; for updates on Avaya.
2 Consult "Avaya's Chapter 11 Debt Restructuring Filing Requires Risk Mitigation for Unified Communications and Contact Center Customers" for strategies to mitigate.
Evaluation Criteria Definitions
Product_Service:__ Core goods and services offered by the vendor for the defined market. This includes current product_service capabilities, quality, feature sets, skills and so on, whether offered natively or through OEM agreements/partnerships as defined in the market definition and detailed in the subcriteria.
Overall Viability: Viability includes an assessment of the overall organization's financial health, the financial and practical success of the business unit, and the likelihood that the individual business unit will continue investing in the product, will continue offering the product and will advance the state of the art within the organization's portfolio of products.
Sales Execution/Pricing: The vendor's capabilities in all presales activities and the structure that supports them. This includes deal management, pricing and negotiation, presales support, and the overall effectiveness of the sales channel.
Market Responsiveness/Record: Ability to respond, change direction, be flexible and achieve competitive success as opportunities develop, competitors act, customer needs evolve and market dynamics change. This criterion also considers the vendor's history of responsiveness.
Marketing Execution: The clarity, quality, creativity and efficacy of programs designed to deliver the organization's message to influence the market, promote the brand and business, increase awareness of the products, and establish a positive identification with the product/brand and organization in the minds of buyers. This "mind share" can be driven by a combination of publicity, promotional initiatives, thought leadership, word of mouth and sales activities.
Customer Experience: Relationships, products and services/programs that enable clients to be successful with the products evaluated. Specifically, this includes the ways customers receive technical support or account support. This can also include ancillary tools, customer support programs (and the quality thereof), availability of user groups, service-level agreements and so on.
Operations: The ability of the organization to meet its goals and commitments. Factors include the quality of the organizational structure, including skills, experiences, programs, systems and other vehicles that enable the organization to operate effectively and efficiently on an ongoing basis.
Completeness of Vision
Market Understanding: Ability of the vendor to understand buyers' wants and needs and to translate those into products and services. Vendors that show the highest degree of vision listen to and understand buyers' wants and needs, and can shape or enhance those with their added vision.
Marketing Strategy: A clear, differentiated set of messages consistently communicated throughout the organization and externalized through the website, advertising, customer programs and positioning statements.
Sales Strategy: The strategy for selling products that uses the appropriate network of direct and indirect sales, marketing, service, and communication affiliates that extend the scope and depth of market reach, skills, expertise, technologies, services and the customer base.
Offering (Product) Strategy: The vendor's approach to product development and delivery that emphasizes differentiation, functionality, methodology and feature sets as they map to current and future requirements.
Business Model: The soundness and logic of the vendor's underlying business proposition.
Vertical/Industry Strategy: The vendor's strategy to direct resources, skills and offerings to meet the specific needs of individual market segments, including vertical markets.
Innovation: Direct, related, complementary and synergistic layouts of resources, expertise or capital for investment, consolidation, defensive or pre-emptive purposes.
Geographic Strategy: The vendor's strategy to direct resources, skills and offerings to meet the specific needs of geographies outside the "home" or native geography, either directly or through partners, channels and subsidiaries as appropriate for that geography and market.
使用 OAuth 2 和 JWT 为微服务提供安全保障
作者 freewolf
使用 OAuth 2 和 JWT 为微服务提供安全保障 - freewolf自留地 - SegmentFault
关键词
微服务、Spring Cloud、OAuth 2.0、JWT、Spring Security、SSO、UAA
写在前面
作为从业了十多年的IT行业和程序的老司机,今天如果你说你不懂微服务,都不好意思说自己的做软件的。SOA喊了多年,无人不知,但又有多少系统开发真正的SOA了呢?但是好像一夜之间所有人都投入了微服务的怀抱。
作为目前最主流的“微服务框架”,Spring Cloud发展速度很快,成为了最全面的微服务解决方案。不管什么软件体系,什么框架,安全永远是不可能绕开的话题,我也把它作为我最近一段时间研究微服务的开篇。
老话题!“如何才能在微服务体系中保证安全?”,为了达成目标,这里采用一个简单而可行方式来保护 Spring Cloud 中服务的安全,也就是建立统一的用户授权中心。
这里补充说一下什么是 Authentication(认证) 和 Authorization(鉴权) ,其实很简单,认证关心你是谁,鉴权关心你能干什么。举个大家一致都再说的例子,如果你去机场乘机,你持有的护照代表你的身份,这是认证,你的机票就是你的权限,你能干什么。
学习微服务并不是一个简单的探索过程,这不得学习很多新的知识,其实不管是按照DDD(Domain Driven Design)领域驱动设计中领域模型的方式,还是将微服务拆分成更小的粒度。都会遇到很多新的问题和以前一直都没解决很好的问题。随着不断的思考,随着熟悉 Facebook/GitHub/AWS 这些机构是如何保护内部资源,答案也逐渐浮出水面。
为了高效的实现这个目标,这里采用 OAuth 2 和 JWT(JSON Web Tokens) 技术作为解决方案,
为什么使用 OAuth 2
尽管微服务在现代软件开发中还算一个新鲜事物,但是 OAuth 2 已经是一个广泛使用的授权技术,它让Web开发者在自己提供服务中,用一种安全的方式直访问 Google/Facebook/GitHub 平台用户信息。但在我开始阐述细节之前,我将揭开聚焦到本文真正的主题: 云安全
那么在云服务中对用户访问资源的控制,我们一般都怎么做呢?然我举一些大家似乎都用过的但又不是很完美的例子。
我们可以设置边界服务器或者带认证功能的反向代理服务器,假设所有访问请求都发给它。通过认证后,转发给内部相应的服务器。一般在 Spring MVC Security 开发中几乎都会这样做的。但这并不安全,最重要的是,一旦是有人从内部攻击,你的数据毫无安全性。
其他方式:我们为所有服务建立统一的权限数据库,并在每次请求前对用户进行鉴权,听起来某些方面的确有点愚蠢,但实际上这确实是一个可行的安全方案。
更好的方式: 用户通过授权服务来实现鉴权,把用户访问Session映射成一个 Token 。所有远程访问资源服务器相关的API必须提供 Token 。然后资源服务器访问授权服务来识别 Token ,得知 Token 属于哪个用户,并了解通过这个Token可以访问什么资源。
这听起来是个不错的方案,对不?但是如何保证 Token 的安全传输?如何区分是用户访问还是其他服务访问?这肯定是我们关心的问题。
所以上述种种问题让我们选择使用 OAuth 2 ,其实访问 Facebook/Google 的敏感数据和访问我们自己后端受保护数据没什么区别,并且他们已经使用这样的解决方案很多年,我们只要遵循这些方法就好了。
OAuth 2 是如何工作的
如果你了解 OAuth 2 相关的原理,那么在部署 OAuth 2 是非常容易的。
让我们描述下这样一个场景,“ 某App 希望获得 Tom 在 Facebook 上相关的数据”
OAuth 2 在整个流程中有四种角色:
资源拥有者(Resource Owner) - 这里是Tom
资源服务器(Resource Server) - 这里是Facebook
授权服务器(Authorization Server) - 这里当然还是Facebook,因为Facebook有相关数据
客户端(Client) - 这里是某App
当 Tom 试图登录 Facebook , 某App 将他重定向到 Facebook 的授权服务器,当 Tom 登录成功,并且许可自己的Email和个人信息被 某App 获取。这两个资源被定义成一个 Scope(权限范围) ,一旦准许, 某App 的开发者就可以申请访问权限范围中定义的这两个资源。
+--------+ +---------------+
| |--(A)- Authorization Request ->| Resource |
| | | Owner |
| |<-(B)-- Authorization Grant ---| |
| | +---------------+
| |
| | +---------------+
| |--(C)-- Authorization Grant -->| Authorization |
| Client | | Server |
| |<-(D)----- Access Token -------| |
| | +---------------+
| |
| | +---------------+
| |--(E)----- Access Token ------>| Resource |
| | | Server |
| |<-(F)--- Protected Resource ---| |
+--------+ +---------------+
Tom 允许了权限请求,再次通过重定向返回 某App ,重定向返回时携带了一个 Access Token(访问令牌) ,接下来 某App 就可以通过这个 Access Token 从 Facebook 直接获取相关的授权资源(也就是Email和个人信息),而无需重新做 Tom 相关的鉴权。而且每当 Tom 登录了 某App ,都可以通过之前获得的 Access Token ,直接获取相关授权资源。
到目前为止,我们如何直接将以上内容用于实际的例子中? OAuth 2 十分友好,并容易部署,所有交互都是关于客户端和权限范围的。
OAuth 2中的客户端和权限范围和我们平时的用户和权限是否相同?我需要将授权映射到权限范围中或将用户映射到客户端中?
为什么我需要客户端?
你也许在之前在类似的企业级开发案例中尝试映射过相关的角色。这会很棘手!
任何类型的应用都提供用户登录,登录结果是一个 Access Token ,所有的之后的API调用都将这个 Access Token 加入HTTP请求头中,被调用服务去授权服务器验证 Access Token 并获取该Token可访问的权限信息。这样一来,所有服务的访问都会请求另外的服务来完成鉴权。
权限范围和角色,客户端和用户
在 OAuth 2 中,你可以定义哪个应用(网站、移动客户端、桌面应用、其他)可以访问那些资源。这里只有一个尺寸,来自哪里的哪个用户可以访问那些数据,当然也是哪个应用或者服务可以访问那些资源。换一种说法,权限范围就是控制那些端点对客户端可见,或者用户根据他的权限来获取相关的数据。
在一个在线商店中,前端可以看做一个客户端,可以访问商品、订单和客户信息,但后端可以关于物流和合同等,另一方面,用户可以访问一个服务但并不是全部的数据,这可以是因为用户正在使用Web应用,当他不能的时候,其他用户却可以。服务之间的访问时我们要讨论的另一个维度。如果你熟悉数学,我可以说在 OAuth 2 中,客户端-权限范围关系是线性独立于用户-权限关系。
为什么是JWT
OAuth 2 并不关心去哪找 Access Token 和把它存在什么地方的,生成随机字符串并保存 Token 相关的数据到这些字符串中保存好。通过一个令牌端点,其他服务可能会关心这个 Token 是否有效,它可以通过哪些权限。这就是用户信息URL方法,授权服务器为了获取用户信息转换为资源服务器。
当我们谈及微服务时,我们需要找一个 Token 存储的方式,来保证授权服务器可以被水平扩展,尽管这是一个很复杂的任务。所有访问微服务资源的请求都在Http Header中携带 Token ,被访问的服务接下来再去请求授权服务器验证 Token 的有效性,目前这种方式,我们需要两次或者更多次的请求,但这是为了安全性也没什么其他办法。但扩展 Token 存储会很大影响我们系统的可扩展性,这是我们引入 JWT(读jot) 的原因。
+-----------+ +-------------+
| | 1-Request Authorization | |
| |------------------------------------>| |
| | grant_type&username&password | |--+
| | |Authorization| | 2-Gen
| Client | |Service | | JWT
| | 3-Response Authorization | |<-+
| |<------------------------------------| Private Key |
| | access_token / refresh_token | |
| | token_type / expire_in / jti | |
+-----------+ +-------------+
简短来说,响应一个用户请求时,将用户信息和授权范围序列化后放入一个JSON字符串,然后使用Base64进行编码,最终在授权服务器用 私钥 对这个字符串进行签名,得到一个 JSON Web Token ,我们可以像使用 Access Token 一样的直接使用它,假设其他所有的资源服务器都将持有一个RSA公钥。当资源服务器接收到这个在Http Header中存有 Token 的请求,资源服务器就可以拿到这个 Token ,并验证它是否使用正确的私钥签名(是否经过授权服务器签名,也就是 验签 )。 验签 通过,反序列化后就拿到 OAuth 2 的验证信息。
验证服务器返回的信息可以是以下内容:
access_token - 访问令牌,用于资源访问
refresh_token - 当访问令牌失效,使用这个令牌重新获取访问令牌
token_type - 令牌类型,这里是
Bearer也就是基本HTTP认证expire_in - 过期时间
jti - JWT ID
由于 Access Token 是 Base64编码 ,反编码后就是下面的格式,标准的JWT格式。也就是 Header、 Payload、Signature 三部分。
{ "alg":"RS256", "typ":"JWT"
}
{ "exp": 1492873315, "user_name": "reader", "authorities": [ "AURH_READ" ], "jti": "8f2d40eb-0d75-44df-a8cc-8c37320e3548", "client_id": "web_app", "scope": [ "FOO" ]
}
&:lƧs)ۡ-[+
F"2"Kآ8ۓٞ:u9ٴ̯ޡ 9Q32Zƌ$ec{3mxJh0DF庖[!뀭N)㥔knVVĖV|夻ׄE㍫}Ŝf9>'<蕱굤Bۋеϵov虀DӨ8C4K}Emޢ YVcaqIW&*uʝub!*Ť\՟-{ʖX܌WTq
使用JWT可以简单的传输 Token ,用 RSA签名 保证 Token 很难被伪造。 Access Token 字符串中包含用户信息和权限范围,我们所需的全部信息都有了,所以不需要维护 Token 存储,资源服务器也不必要求 Token 检查。
+-----------+ +-----------+
| | 1-Request Resource | |
| |----------------------------------->| |
| | Authorization: bearer Access Token | |--+
| | | Resource | | 2-Verify
| Client | | Service | | Token
| | 3-Response Resource | |<-+
| |<-----------------------------------| Public Key|
| | | |
+-----------+ +-----------+
所以,在微服务中使用 OAuth 2 ,不会影响到整体架构的可扩展性。淡然这里还有一些问题没有涉及,例如 Access Token 过期后,使用 Refresh Token 到认证服务器重新获取 Access Token 等,后面会有具体的例子来展开讨论这些问题。
如果您感兴趣,后面还会有实现部分,敬请期待~
由于 http://asciiflow.com/ 流程图使用中文就无法对齐了,本文中流程图都是英文了~
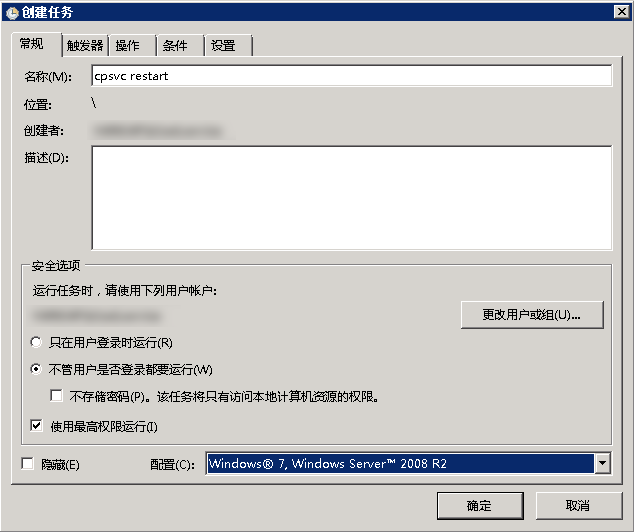
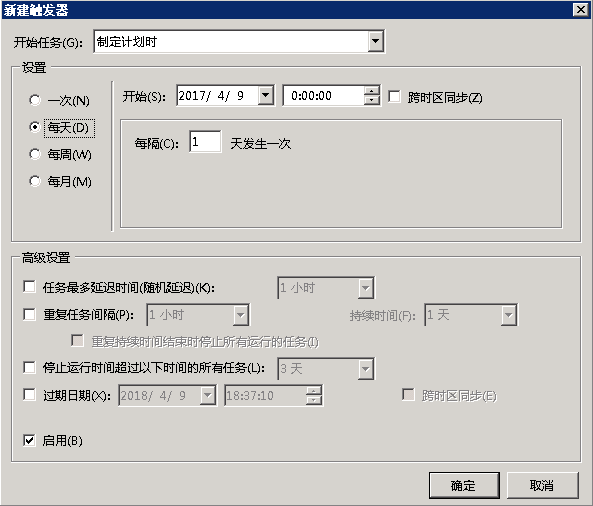
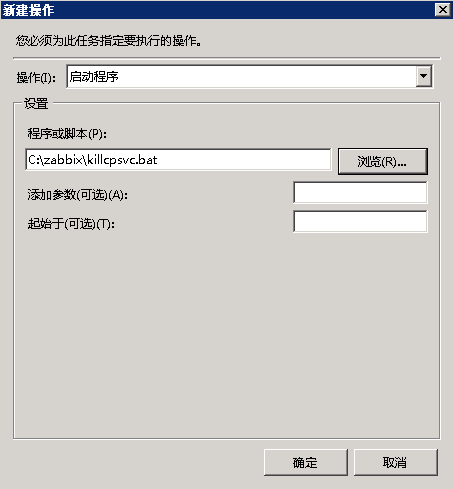
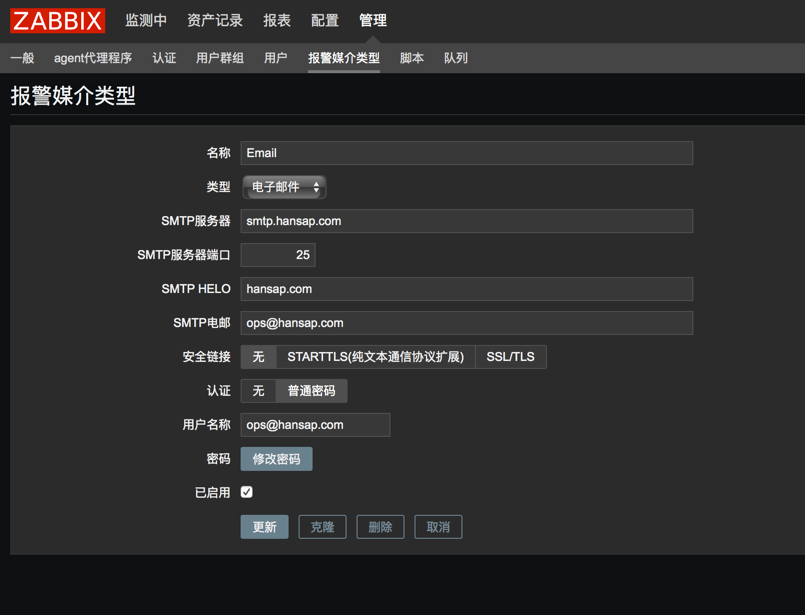
ZABBIX在windows下面的问题汇总
ZABBIX 客户端和ZABBIX proxy
当服务器不多的时候,使用ZABBIX server直接收集是没有问题的,但是当服务器数量到达一定量级的时候,可能会导致zabbix出现性能问题,导致的情况有:
- Web操作很卡,容易出现502
- 图层断裂
- 开启的进程(Pollar)太多,即使减少item数量,以后加入一定量的机器也会有问题
同时ZABBIX还可以同时实现集中、分布式监控,包括场景:
- 监控远程区域设备
- 监控本地网络不稳定区域
- 当 Zabbix 监控上千设备时,使用它来减轻 Server 的压力
- 简化 Zabbix 的维护
架构图
参考 zabbix proxy分布式监控配置(45) - 运维生存时间
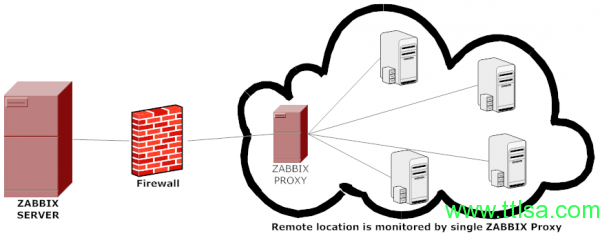
这样可以将不同段的交给不同的ZABBIX proxy,保证ZABBIX server的单一性,也减少性能消耗。
ZABBIX监控windows日志需要采用主动式的方推送日志信息。 ZABBIX的客户端监控分为几种类型,zabbix客户端、zabbix客户端(主动式)。
Zabbix Proxy 仅仅需要一条 TCP 连接到 Zabbix Server,所以防火墙上仅仅需要加上一条规则即可。
Zabbix Proxy 数据库必须和 Zabbix Server 分开,否则数据会被破坏,毕竟这两个数据库的表大部分都相同。
总之记住,数据库分开即可。
Zabbix Proxy 收集到数据之后,首先将数据缓存在本地,然后在一定的时间之后传递给 Zabbix Server。
这个时间由 Zabbix Proxy 配置文件中参数 ProxyLocalBuffer and ProxyOfflineBuffer 决定。
Zabbix Proxy 是一个数据收集器,它不计算触发器、不处理事件、不发送报警。
安装
参考 Zabbix 配置 Proxy 代理监控 - Jamin Zhang
1. 安装 Zabbix Proxy
yum install mariadb-server zabbix-proxy-mysql
2. 创建及初始化数据库
3. 启动数据库
systemctl start mariadb
创建配置 Zabbix Proxy 数据库及用户
create database zabbix_proxy character set utf8 collate utf8_bin;
grant all privileges on zabbix_proxy.* to zabbix_proxy@localhost identified by ‘zabbix_proxy’;
flush privileges;
导入 sql
cd /usr/share/doc/zabbix-proxy-mysql-3.0.3
zcat schema.sql.gz | mysql -uroot zabbix_proxy
配置 zabbix_proxy.conf
配置如下:
[root@linux-node2 ~]# grep “^[a-Z]” /etc/zabbix/zabbix_proxy.conf
Server=192.168.56.11
Hostname=Zabbix proxy
LogFile=/var/log/zabbix/zabbix_proxy.log
LogFileSize=0
PidFile=/var/run/zabbix/zabbix_proxy.pid
DBHost=localhost
DBName=zabbix_proxy
DBUser=zabbix_proxy
DBPassword=zabbix_proxy
SNMPTrapperFile=/var/log/snmptrap/snmptrap.log
Timeout=4
ExternalScripts=/usr/lib/zabbix/externalscripts
LogSlowQueries=3000
启动 Zabbix Proxy 服务
systemctl start zabbix-proxy
在 Zabbix Web 界面中配置 Zabbix Proxy
定位到 Administration -> Proxies -> Create proxy 主要配置如下选项:
Proxy name: 即 Zabbix Proxy 的 hostname
Proxy mode: 即 Zabbix Proxy 的工作模式,默认为主动模式
Hosts Proxy hosts: 选择哪些机器处于 Proxy 模式
添加 Proxy 架构的主机监控
添加主机的方式和正常模式一样,唯一不同的是 Monitored by proxy 选择对应的 Proxy 节点。
注意
如果是已经存在的没有被 Proxy 监控的节点,修改成被 Proxy 代理监控时,
需要修改 Zabbix Agent 配置文件,将 Server/ServerActive 配置成 Proxy 的 IP
ZABBIX proxy的主动模式和被动模式
参考 zabbix主动被动模式说明/区别 – 酷喃|coolnull|
说明:
使用zabbix代理有很多好处,一方面可以监控不可达的远程区域;另一方面当监控项目数以万计的时候使用代理可以有效分担zabbix server压力,也简化分布式监控的维护。
具体:
主动、被动模式都是相对于proxy来说的。proxy主动发送数据就是主动模式;proxy等待server的请求,再发送数据就是被动模式。因为主动模式可以有效减轻zabbix server压力,需要监控的东西很多时一定要把监控模式更改为主动监控
被动模式流程,被动模式一定要记得设置Server = ServerIP
被动模式工作流程:
Server 打开一个TCP连接
Server发送一个key 为agent.ping
Agent接受这个请求,然后响应< HEADER >< DATALEN >
Server对接受到的数据进行处理
TCP连接关闭
主动模式流程,主动模式一定要记得设置ServerActive=ServerIP
Agent向Server建立一个TCP连接
Agent请求需要检测的数据列表
Server响应Agent,发送一个Items列表
Agent允许响应
TCP连接完成本次会话关闭
Agent开始周期性地收集数据
zabbix agentd主动和被动模式的区别
zabbix proxy 解决代替Server端监控的问题,ZABBIX anget作为服务器上的监控代理,同样也有不同模式的监控方式。同时agentd这种由客户端自动上报的方式,也可以部分解决性能的问题.
1. Agentd的配置调整:
LogFile=/tmp/zabbix_agentd.log
Server=14.18.xxx.xxx
ServerActive=14.18.xxx.xx
Hostname=119.146.xxx.xx
RefreshActiveChecks=60
BufferSize=10000
MaxLinesPerSecond=200
Timeout=30
比较重要的参数是ServerActive和Hostname,ServerActive是指定Agentd收集的数据往哪里发送,Hostname是必须要和Server端添加主机时的主机名对应起来,这样Server端接收到数据才能找到对应关系,我这里为了兼容被动模式,没有把StartAgents设为0,如果一开始就是使用主动模式的话建议把StartAgents设为0,关闭被动模式
二、Server的配置调整:
StartPollers=100
首先把这个主动收集数据进程减少,原来开到700多,囧
StartTrappers=200
然后把这个负责处理Agentd推送过来的数据的进程开大一些,就可以了
三、调整模板
建议完整克隆一个Template OS Linux 模板来改,需要调整的地方就是:
wKiom1Q48kiA3gVIAAI9T4EdOKk715.jpg把所有的item的类型由原来的“zabbix代理”改成“zabbix端点代理程序(主动式)”
zabbix 监控windows下面的事件日志
1. 监控项配置
zabbix 日志使用zabbix客户端(主动式)来进行收集,如果使用其他的模式是没有办法收集到的,配置完成后会报错。
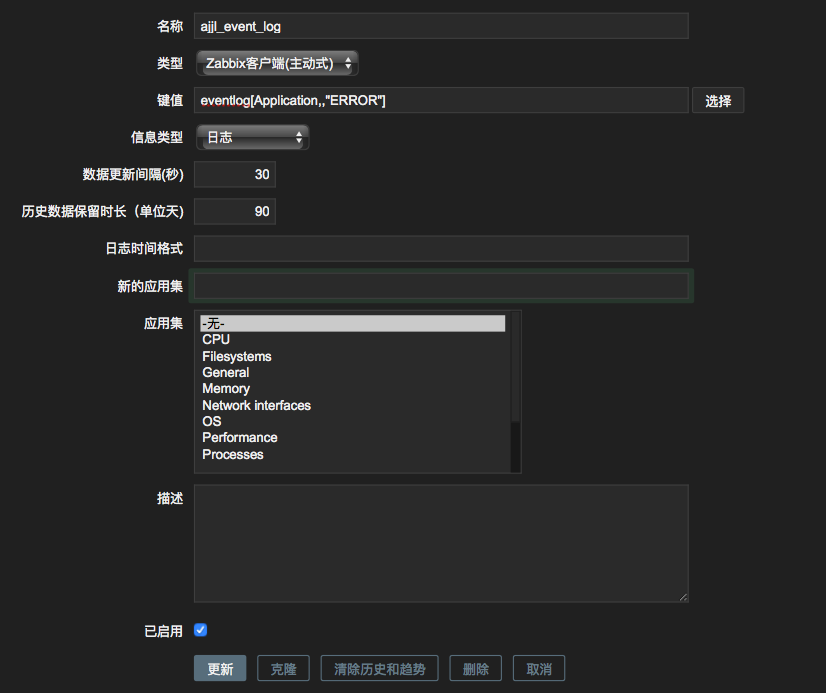
记得一定要使用ZABBIX客户端(主动式)和信息类型为日志型的才可以抓取到相关日志
使用eventlog就可以获取相应的日志信息,其他更多函数可以参考如下ZABBIX文档
Windows-specific item keys Zabbix Documentation 3.2
这个里面收录了一些windows的单独的文档。如果需要调windows的内容需要在这里来找,可以发现很多监控项实际上是不支持的。
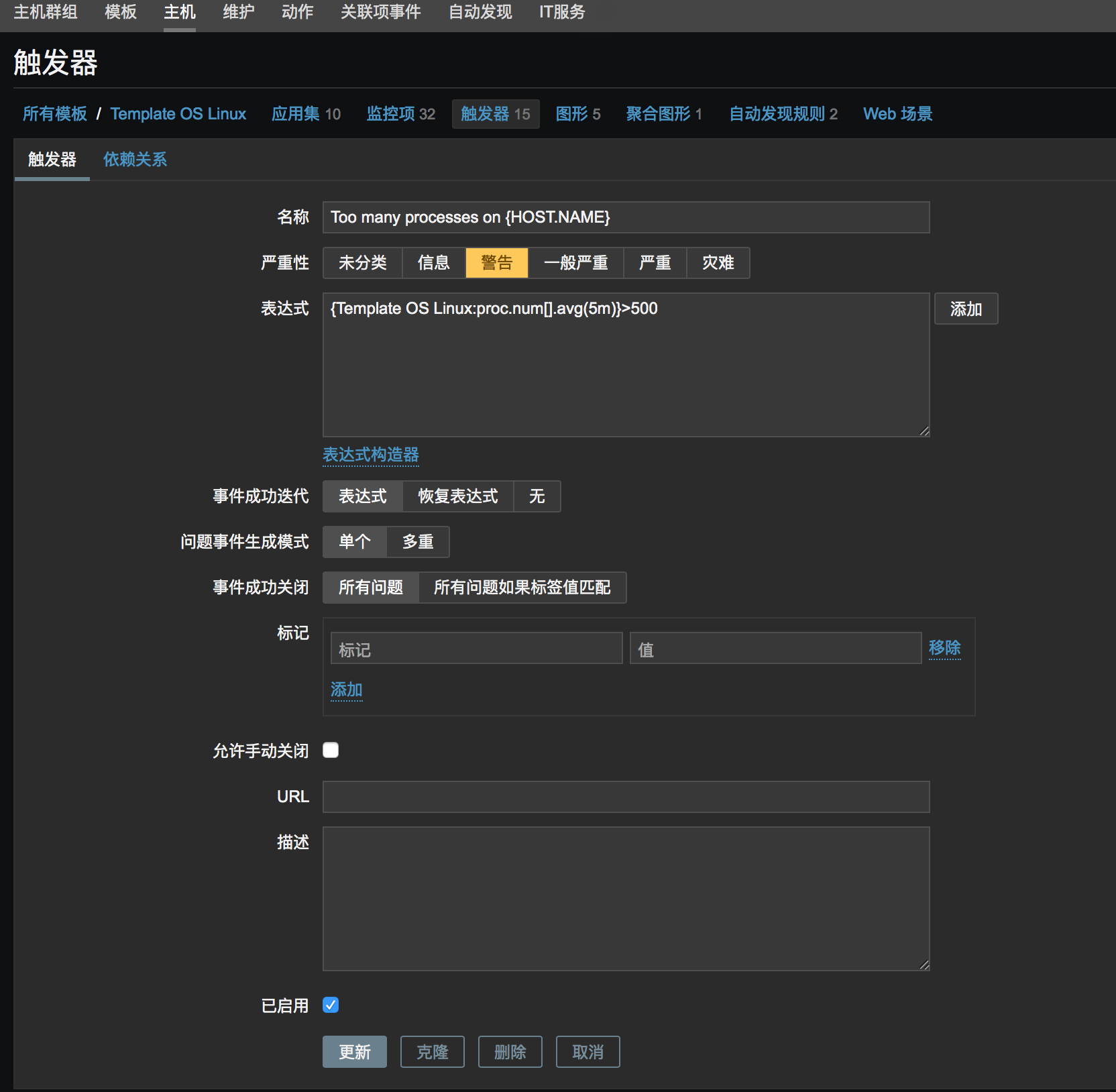
2. 触发器配置
监控项配置完了之后可以对日志进行触发器配置,可以
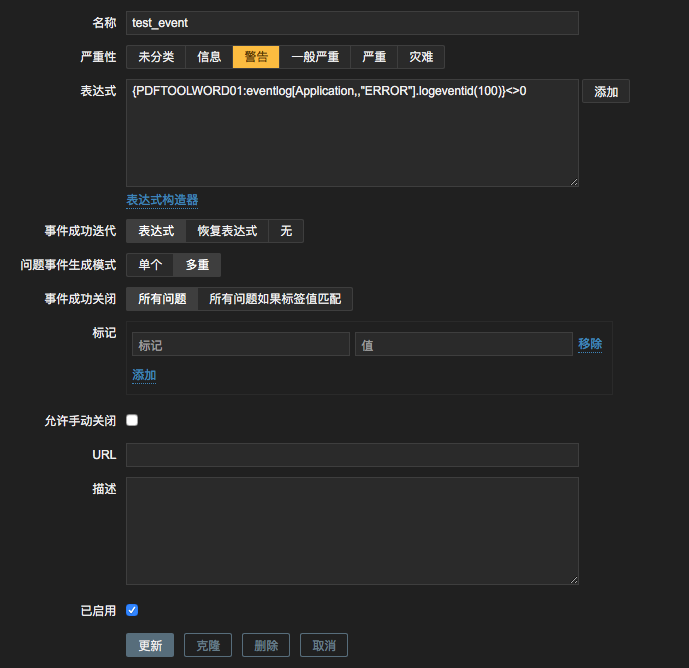
表达式中可以采取另外的几种写法,来抓取不同的事件
3. 配置动作
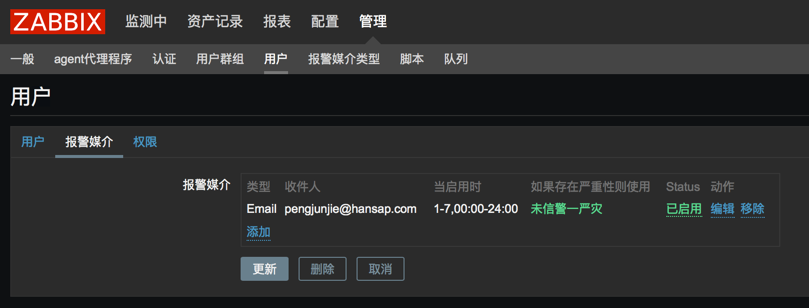
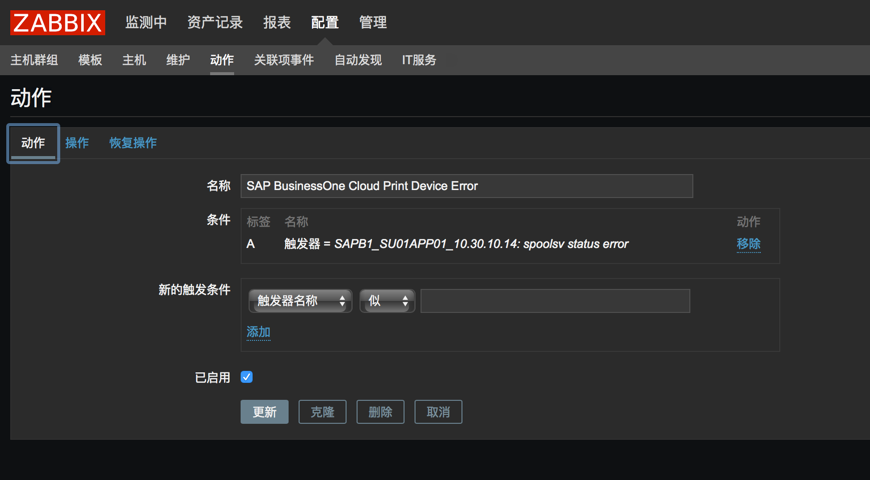
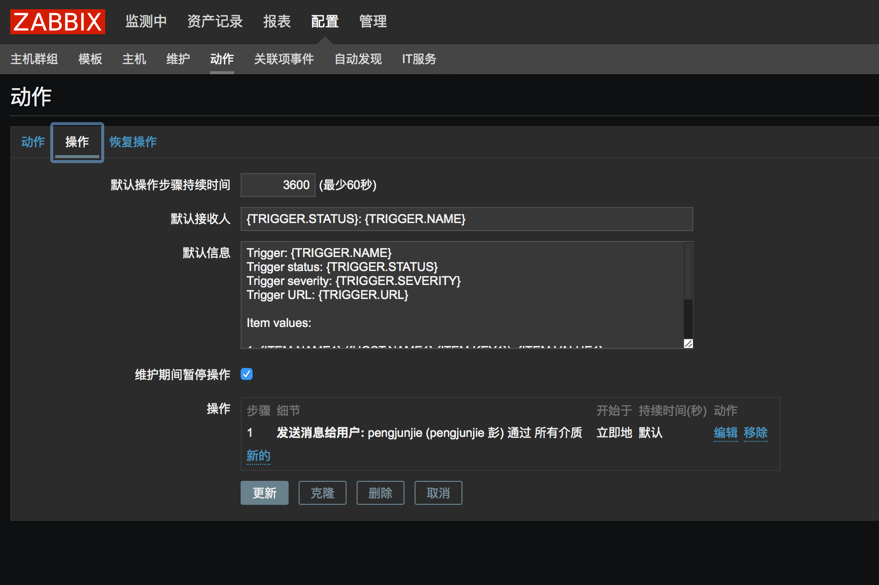
配置动作其实跟这个没关,主要解决了几个事情,也大概的总结一下
ZABBIX动作主要在操作中设置,其中可以定义集中操作模式。在每个动作里面可以执行多条操作步骤,建议每天操作步骤只写一条语句,在写多条的时候总是会发现有时候只会执行其中的一条。所以尽量的使用多条操作命令,这样另外的一点好处是在操作步骤的时候可以定义多个步骤,以及多个步骤的执行顺序和关系。
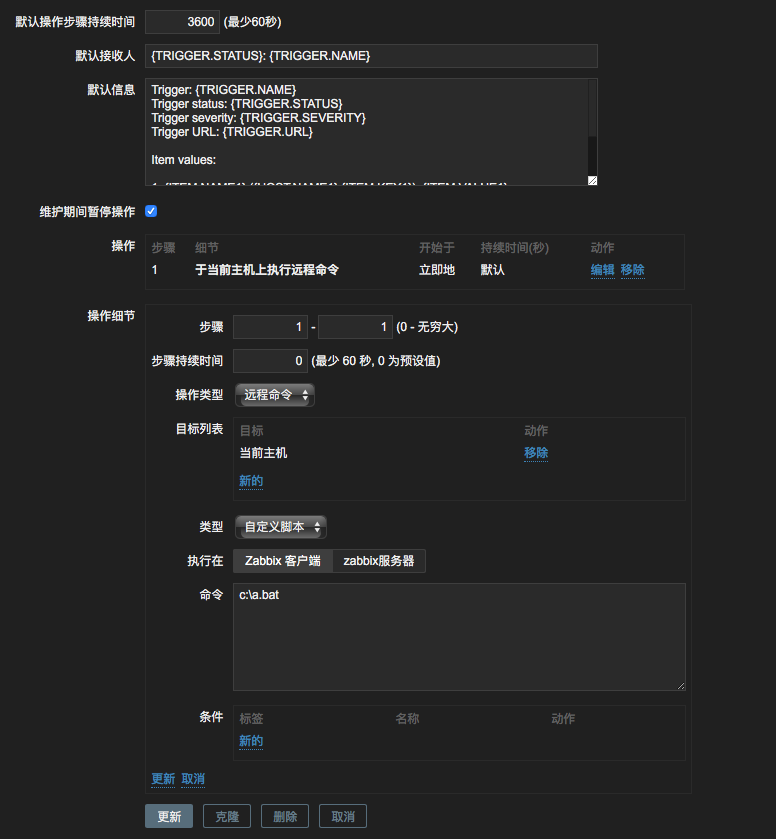

几个选项也请记住,如步骤持续时间、操作类型、目标列表、类型。 如果是windows的脚本请选择自定义脚本。
在命令中可以执行命令也可以使用bat文件去执行bat批处理,一些操作用bat来处理
zabbix windows的远程命令的原理
由于应用场景想用ZABBIX从远程拉起一些需要界面交互的软件,所以试着用ZABBIX去处理,但是都会有问题。
- 模式一:用ZABBIX的命令里面配置直接启动,以及使用bat启动。
- 在这种模式下,都会以system 用户去启动window的EXE文件,所以此时是不会出现administrator的界面交互框的。
- 尝试使用工具进行以admin用户启动,测试后发现也是以system用户去实现的。
- 模式二:将EXE文件转成服务来启动
- 转换为服务之后使用服务启动,不管是用本地用户还是admin用户,启动后都不会有窗口弹出。
原理解析:
大概的想法就是使用远程命令的时候,实际和linux类似,是在命令下面执行的,此时是不能和桌面进行交互的,所以会一直使用System,这两边是没有办法关联到一起的。
解决方法:
暂时还是使用zabbix来停止程序,有admin下面的控制程序来监控如果进程没有了,自动拉起来,这样就可以拉起交互软件。
以Admin模式运行windows bat文件
在CMD中或者在bat中有时候想要以admin模式运行,使用run as可以解决问题,但是使用run as 需要手动输入管理员的密码,在某些无法交互的场景不能使用,所以我们需要可以直接写入密码的方法。网上的相关解决方案很多,使用了很多,也有很多无法使用。就留下了一个唯一可以使用的方法,虽然没有最终的解决想要解决的问题,但是可以预留下来留给后面使用。
工具链接如下
CPAU
使用起来也比较简单
c:\CPAU.exe -u administrator -p ******* -ex "C:\Program Files (x86)\***\*.exe" -lwp
这样就可以用管理员模式运行
zabbix 监控项
ZABBIX开通的监控windows的内容
Windows-specific item keys Zabbix Documentation 3.0
我们当前使用的3.2版本
Windows-specific item keys Zabbix Documentation 3.2
上面的标识的是3.0版本的
Copyright © 2020 鄂ICP备16010598号-1